Understanding the different rebooting options and their implications allows users and IT support professionals to maintain the stability and efficiency of devices while safeguarding critical data and files.
 What is Rebooting?
What is Rebooting?
Rebooting refers to the process of restarting a computer or electronic device to refresh its operating system, clear temporary data, and resolve various software or hardware issues.
What is the Benefit of Rebooting?
It is a common troubleshooting step to resolve problems such as system freezes, slow performance, or software glitches. Rebooting can also be performed as part of routine maintenance to keep the system running smoothly.
 How Many Different Types of Reboots Are There?
How Many Different Types of Reboots Are There?
There are two primary types of reboot protocols:
- Hard reboot
- Soft reboot
A hard reboot, also known as a hard reset or force restart, involves forcibly powering off the device and then turning it back on. Hard reboots do not shut down the operating system or close applications correctly, leading to potential data loss or file corruption. However, the hard reboot is effective in situations where the system is unresponsive or frozen.
The soft reboot, also known as simply “reboot,” involves restarting the device using software commands. The process allows the operating system to perform a proper shutdown by closing running applications and saving necessary data before restarting. Soft reboots are less likely to cause data loss or corruption compared to hard reboots.
What is Sleep Mode?
In sleep mode, the computer or device enters a low-power state. While in this mode, the screen and other components are turned off to save energy. The system remains in a partially active state, allowing quick wake-up times.
During sleep, the operating system and running applications are stored in memory, so the device can quickly resume its previous state when awakened. You’ll be able to pick right back up where you left off with minimal downtime since you don’t have to wait for a time-consuming reboot.
Sleep mode consumes minimal power and is most useful for short periods of inactivity. However, for standard machines, too much sleep might not be great for overall performance.
Turning your computer off completely at least once a week is a best practice to refresh your machine’s operations.
What Happens When My Computer Hibernates?
Hibernate is a deeper power-saving state than sleep. When a computer hibernates, the contents of its RAM (random-access memory) are saved to the hard drive or SSD, allowing the system to power down completely.
Powering down helps to conserve energy while preserving the open applications and data. When the computer is powered back on, it restores the saved state from the disk to RAM, resuming the system to where it was before entering hibernation.
What Happens During the Reboot Process?
During the reboot process, whether it’s a hard or soft reboot, the operating system goes through its boot sequence:
- initializing hardware
- loading essential system files
- launching necessary services
This process helps the system regain reliability by clearing temporary data and freeing up resources that might have been tied up by malfunctioning applications or processes. It also allows the operating system to start fresh, potentially resolving any software-related issues.
 Are There Risks Associated with Rebooting Your System?
Are There Risks Associated with Rebooting Your System?
As mentioned earlier, a hard reboot doesn’t allow applications and the operating system to save data properly before shutting down. This sudden interruption can lead to data loss or corruption, especially if important files were not saved at the time of the hard reset.
Potential loss of critical data is why it’s generally recommended to use soft reboots whenever possible, because they allow the system to shut down properly, reducing overall risk.
 How Can Virtualized Desktops Reduce Reboot Related Data Risk?
How Can Virtualized Desktops Reduce Reboot Related Data Risk?
When end users are using virtual desktop infrastructure (VDI) solutions, the actual computing and processing occur on remote servers rather than their local machines. When using VDI, the end user interacts with a virtual desktop hosted on a server, which allows for better management, security, and data protection.
Since the virtual desktop environment is hosted remotely, there isn’t direct access to the underlying hardware or power controls.
This means users cannot perform hard resets or forcibly shut down their virtual machines like they might do with traditional physical PCs. Instead, they typically have controlled ways of shutting down or rebooting the virtual desktop through the VDI software, allowing for a more structured and less risky process.
In Conclusion
Rebooting is a fundamental process used to refresh, troubleshoot, and maintain the reliability of personal computers and electronic devices.
A hard reboot, though effective in resolving unresponsive systems, carries the risk of data loss and file corruption due to its abrupt nature while a soft reboot offers a more graceful approach, reducing the likelihood of data loss by allowing applications to close properly before restarting.
Sleep and hibernate modes are power-saving alternatives, with hibernate offering greater energy conservation while preserving the system’s state.
The adoption of virtualized desktops means users are less likely to unintentionally cause downtime and data loss, as there are controlled methods for shutting down or rebooting virtual machines.
We Have Experts on Staff to Answer Your Questions Optimizing System Performance
Interested in finding out how partnering with an award-winning cloud hosting provider can help you achieve your business goals while reducing your overall technology costs?
Our trained team of cloud computing experts can help by answering all your questions about how to align your technology with industry guidelines and while maintaining strict compliance standards.
We’ll show you how to use our efficient cloud-based storage and processing solutions in your business to improve your security, productivity, and profitability.
Let us demonstrate exactly what CyberlinkASP can do for you – using your own data and workflows.
What is an Operating System?Operating Systems and Cloud Hosting for Your Business
The operating system (OS) you use can have a profound impact on the overall performance, reliability, and success of your cloud services. Choosing the right OS is critical for optimal efficiency, security, and cost-effectiveness.
 What is an Operating System?
What is an Operating System?
An operating system is the essential software enabling computers to function by managing hardware resources, coordinating software applications, and providing user interfaces. Without an operating system, your computer isn’t able to perform any functions.
The OS serves as an intermediary between users and computer hardware, delivering smooth operations and maintaining security. Most operating systems come pre-loaded into a machine and today’s modern operating systems are designed to be easy to use.
Other terminology you might run across when investigating your computer’s operating system is the graphical user interface (GUI) which is pronounced as “gooey”.
Common Operating Systems: An Overview
Whether you use a computer for home or business use, it relies on an operating system. Even your mobile devices have an OS. In both personal and professional settings, several operating systems are widely used.
The three most popular operating systems are:
- Microsoft Windows
- macOS
- Linux
Known for its user-friendly interface, Microsoft Windows is extensively used in both personal computers and business environments. In fact, nearly 1.4 million active devices run off Windows 10 and 11. This puts Microsoft firmly in first place.
The second-place position goes to Apple’s macOS. The operating system, often named for popular California landmarks, is designed exclusively for use in the company’s popular Macintosh computers.
Linux is an open-source operating system, renowned for its robustness, flexibility, and security features. One hundred percent of the world’s “super computers” use Linux, but for companies with standard computers? Linux accounts for around 2% of market share among average PC users.
Mobile operating systems like Google’s Android and Apple’s iOS power smartphones and tablets.
 Identifying Your Computer’s Operating System
Identifying Your Computer’s Operating System
The process for identifying the OS running on your computer varies depending on the operating system in use:
For Windows: Press the Windows key + R, type “winver,” and press Enter to reveal your Windows version information.
For macOS: Click on the Apple icon in the top left corner and select “About This Mac” to view your macOS version information.
For Linux: Open a Terminal window, type “lsb_release -a,” and press Enter to display your Linux distribution information.
Your IT department can provide additional information if your business servers run a different operating system than your employees’ computers.
 What is the Benefit of Changing the OS of Business Computers?
What is the Benefit of Changing the OS of Business Computers?
While most operating systems come pre-loaded on machines, some businesses may find valid reasons to change their OS driven by factors like:
- performance
- security
- software compatibility
- cost considerations
- vendor support
- employee preferences
Making the right OS choice is essential to optimize a business’s computing environment for its specific needs and objectives.
Switching the operating system (OS) of your business computers can offer several advantages. An OS switch has the potential to improve overall performance and efficiency, as certain OS options are better optimized for specific requirements. In highly regulated industries, changing to a more secure OS can effectively address security concerns and safeguard sensitive data.
Beyond that, the decision to change OS could be influenced by compatibility with specific software applications, cost considerations, availability of vendor support, seamless integration with cloud hosting solutions, hardware upgrades, user preferences, and customization needs.
By carefully considering these factors, businesses can make an informed OS choice that enhances productivity, ensures security, and delivers an improved user experience, all while aligning their computing environment with their business objectives.
 Tailored Cloud Hosting Services for Your Operating System
Tailored Cloud Hosting Services for Your Operating System
Understanding that each business has unique OS needs and preferences, our cloud hosting services extend full support to a wide range of operating systems. Our team of experts will guide you to deliver optimal performance, security, and cost-effectiveness.
In Conclusion
You aren’t locked into the operating system that came loaded on your machines if you have business concerns or objectives that may make a different OS more desirable. By carefully considering factors such as performance, scalability, security, compliance, cost, and compatibility, you can make an informed decision that best suits your organization’s needs.
We understand the significance of the right OS, and our expert team is dedicated to providing a cloud environment that is compatible with your operating system.
With the right OS in place, you can leverage the full potential of cloud technology and drive your business towards greater success and growth.
Need Help Making Your Network More Robust, Increasing Business Productivity, Or Capping Escalating Technology Costs?
Our trained team of cloud computing experts can help you by developing the most secure and efficient cloud-based storage and processing solutions for your business.
Let us demonstrate exactly what Cyberlink can do for you – using your own data and workflows.
Mainframe Computers and Modern Cloud Computing: A Legacy GuideMainframe computers played a significant role in shaping the fundamentals of modern cloud computing. Key principles of scalability, multi-tenancy, reliability, security, and cost-effectiveness were inherent to mainframe systems. Now they are integral to cloud services. While we have made the transformation from physical mainframes to cloud infrastructure, it is important to emphasize their interconnected historical and functional relevance.
 What is a Mainframe Computer?
What is a Mainframe Computer?
A mainframe computer is a high-performance computing system, synonymous with significant processing power, vast storage capacity, and advanced reliability features.
These computers were true behemoths and typically larger than conventional server units. Mainframes held a vise-like grip on the tech industry from the 1950s through to the early 1980s.
They served as the backbone of computing for major organizations such as banks, government institutions, and corporations.
In their prime, mainframe computers were the epitome of advanced computing technology. They were able to handle and process large amounts of data, allowing for concurrent usage by hundreds or even thousands of users.
These features were particularly invaluable to big businesses where data processing requirements were immense and continuous.
 Is the Mainframe Computer Still Relevant Today?
Is the Mainframe Computer Still Relevant Today?
When you look at the computing power of the phone in your hand or back pocket, you might think mainframes have gone the way of the dodo bird.
Contrary to expectations, advancements in technology have not rendered mainframe computers obsolete.
Despite the prevalence of more compact and accessible computing devices, mainframe computers still form an indispensable part of the IT infrastructure in numerous large-scale organizations.
The enduring relevance of the mainframe computer can be attributed to three key features:
- remarkable durability
- superior performance
- top-tier security posture
These qualities remain critical when managing large databases and transaction processing systems.
 The Mainframe’s Relevance in Modern Cloud Computing
The Mainframe’s Relevance in Modern Cloud Computing
Mainframe computers laid the foundation for many of the principles that are fundamental in cloud computing:
Scalability
Mainframes were renowned for their scalable nature, efficiently accommodating increased workloads without disruption. In cloud computing, cloud architecture is designed to offer on-demand resource allocation and scaling based on the user’s requirements.
This scalability provides businesses with flexibility, allowing them to adjust their processing power in real-time, depending on the volume of data they need to handle.
Sharing Resources Efficiently
Mainframe computers could handle requests from multiple users concurrently, a concept that is fundamental to modern cloud environments.
In a cloud setting, multiple tenants share computing resources while still operating independently – a nod to the multi-user capacity of its mainframe predecessors.
This multi-tenancy not only ensures efficient resource use but also provides a cost-effective solution for businesses, typically reducing their operational expenses and improving the efficient use of IT budgets.
Reliability and Uptime
Mainframes have always been associated with reliability and high uptime.
“Always Available, Always On” is a fundamental expectation from end users in today’s cloud computing environment.
Many cloud service providers commit to providing uptime of 99.9% or better, ensuring their customers’ business continuity and productivity.
This philosophy, pioneered by mainframes, is now a standard offering from the best cloud hosting providers.
Safeguarding Critical Data
Security was a robust feature embedded into the design of mainframe computers.
The need for secure data handling and storage has been inherited by cloud computing, with cloud providers continually investing in advanced security measures to protect user data. Using an array of security tools and protocols, cloud computing aims to provide a secure environment for data.
In this way, cloud environments are aligning with the stringent security norms established by mainframe computers.
Cost-Effectiveness
When it came to cost-effectiveness in terms of computing power per dollar, mainframes were pioneers.
This principle has been adopted and improved upon by many cloud providers.
Some offer flexible pay-as-you-go pricing models, allowing organizations to pay for only what they use, minimizing wasted dollars, and maximizing return on investment.
Of course, you should always make sure you understand your service level agreement, so you know your organization is getting what you’ve paid for from your provider. At Cyberlink, our goal is to have a plain language agreement with our partners.
In Conclusion
While the physical prevalence of mainframe computers has reduced, their legacy continues in the principles and practices of modern cloud computing.
The transformation has been more of form than function — from the tangible, room-filling mainframes to the intangible, yet omnipresent cloud.
A deeper appreciation of the cloud and its functionalities comes from understanding the origins and mechanics of mainframe computers.
The innovations and developments that marked the era of mainframes were instrumental in shaping the cloud computing revolution and the benefits it conveys to businesses.
 Need Help Making Your Network More Robust, Increasing Business Productivity, Or Capping Escalating Technology Costs?
Need Help Making Your Network More Robust, Increasing Business Productivity, Or Capping Escalating Technology Costs?
Our trained team of cloud computing experts can help you by developing the most secure and efficient cloud based storage and processing solutions for your business.
Let us demonstrate exactly what Cyberlink can do for you – using your own data and workflows.
Understanding the Role of Virtualization in Cloud ComputingIn cloud computing, virtualization plays a pivotal role. But what is virtualization and how can it benefit your small to mid-sized business?
 What is Virtualization in Cloud Computing?
What is Virtualization in Cloud Computing?
Simply put, virtualization involves creating virtual versions of physical computing resources.
This abstraction from physical hardware offers increased flexibility and scalability. Allowing multiple virtual instances to run concurrently on a single physical machine, maximizes resource utilization.
How is Virtualization Beneficial for SMBs?
Utilizing virtualization can simplify the direct IT demands on your business whether those are budgeting, personnel, or productivity concerns.
Business owners who take advantage of virtualization benefit from:
- Reduction in capital expenses, IT overhead, and operating costs.
- Minimized downtime
- Increased productivity
- Quicker provisioning of resources and applications
Let’s look at specific types of virtualizations commonly offered to small businesses by cloud hosting vendors.
 What is Server Virtualization?
What is Server Virtualization?
Server virtualization divides one physical server into multiple virtual servers. Each of the virtual servers operates independently. This allows it to act as a standalone unit with its own set of resources and operating system.
This leads to optimized resource utilization, reduced costs, and a seamless scale-up of computing capacity based on demand.
How Does Application Virtualization Improve Efficiency?
Application virtualization is another aspect, focusing on isolating applications from the underlying operating system and hardware.
There are two types of application virtualization:
- remote
- streaming
Application virtualization enhances compatibility and streamlines application updates, making software management more efficient and consistent across different platforms.
What is the Impact of Network Virtualization?
There is also an option to use network virtualization. This abstracts the physical network infrastructure, allowing multiple virtual networks to coexist on a shared physical network.
Network virtualization offers flexibility and simplified management, enabling the creation and management of complex networks effortlessly.
 Why Consider Desktop Virtualization?
Why Consider Desktop Virtualization?
Desktop virtualization, also known as Virtual Desktop Infrastructure (VDI), is a technology that detaches the user’s desktop environment from their physical machine. Instead, it is hosted within a virtual environment in the cloud.
This strategy is particularly attractive for SMBs for several reasons:
Desktop virtualization centralizes data storage, so it reduces the risks associated with data loss or theft posed on individual devices. It also facilitates better control over access permissions, enhancing the security of sensitive information.
VDI simplifies the administration of user environments. Changes can be made in one place and automatically applied across all virtual desktops. This not only saves time but also ensures consistency across the organization.
Since the desktop environment is hosted in the cloud, it can be accessed from any device with an internet connection. This promotes flexibility and allows employees to work from anywhere, accommodating remote or offsite work trends.
Instead of manually updating software on each machine, updates and patches can be applied centrally to the virtual desktop environment. This reduces downtime and ensures all users have access to the latest software versions.
With VDI, businesses can extend the lifespan of older hardware or adopt a Bring Your Own Device (BYOD) policy, since the majority of the processing is done in the cloud. This can significantly reduce hardware and maintenance costs.
In the event of a disaster, virtual desktops can be recovered quickly and easily, ensuring minimal disruption to business operations making them a smart part of any organization’s disaster planning.
Read even more about cost savings and security improvements from virtual desktops.
What is Storage Virtualization?
Lastly, storage virtualization abstracts physical storage devices into a unified virtual storage pool. This pool can be allocated as required, improving storage efficiency and enabling advanced features like replication and disaster recovery.
 How Can Virtualization Enhance Security, Scalability, and Resource Efficiency?
How Can Virtualization Enhance Security, Scalability, and Resource Efficiency?
Virtualization offers enhanced security by providing isolation between virtual instances, which mitigates malware spread and data breaches. It also allows SMBs to scale their resources rapidly based on demand, ensuring optimal performance and cost efficiency.
By consolidating multiple virtual instances on a single machine, virtualization maximizes resource utilization. This can reduce hardware costs, minimize power consumption, and optimize your data center footprint, creating a more sustainable IT infrastructure.
How Does Virtualization Simplify IT Management?
Virtualization simplifies IT management by centralizing administration tasks and reducing complexity. It streamlines provisioning, monitoring, and maintenance of virtual resources, saving time, and improving operational efficiency.
In Conclusion
Virtualization is a foundational technology within cloud computing, offering tangible benefits to SMBs in terms of scalability and security.
By understanding and leveraging different types of virtualizations, businesses can fully harness the potential of the cloud by driving growth, increasing productivity, and reducing capital expenditures.
Need Help Making Your Network More Robust, Increasing Business Productivity, Or Capping Escalating Technology Costs?
Our trained team of cloud computing experts can help you by developing the most secure and efficient cloud-based storage and processing solutions for your business.
Let us demonstrate exactly what Cyberlink can do for you – using your own data and workflows.
Optimizing RAM: Suggestions and Solutions for Your BusinessRAM (Random Access Memory) plays a critical role in delivering efficient and high-performance operations. Cloud hosting can be a strategic part of optimizing RAM usage.
RAM: A General Overview
If you think back to your basic computing class, you likely remember that RAM, or Random Access Memory, is a fundamental component of computers. It provides short-term, temporary storage for data and any instructions that the system’s processor needs to access quickly.
Essentially RAM is a bridge between the processor and long-term storage devices, such as your hard disk (HDD) or solid-state drives (SSD). RAM’s role is facilitating quick access to frequently used information and enabling smooth and efficient computing operations.
 How Much RAM Do We Need?
How Much RAM Do We Need?
The average modern computer usually has at least 2GB of RAM – but some machines may top out at 64GB. Your demands may not merit maxing out your memory slots but it’s always a good idea to fully understand demand so you only provision what you realistically need and because more RAM doesn’t always equal improved speed and performance.
A general rule is that a typical office workhorse machine performing standard tasks is 16GB. Tony Polanco, a writer for the popular tech blog Tom’s Guide, says this “gives enough headroom” without holding you back.
The Role of RAM in Business Computing
RAM is crucial in optimizing various business computing functions because it directly impacts:
- speed
- performance
- multitasking capabilities of servers and desktop machines
- productivity and user experiences.
The Right Amount of RAM Delivers Enhanced Performance and Efficiency
Sufficient RAM is essential for businesses to run resource-intensive applications smoothly.
When a computer lacks adequate RAM, it relies on virtual memory, which is significantly slower.
Insufficient RAM is often the culprit behind sluggish performance, system freezes, and decreased productivity.
By having enough RAM, businesses can ensure that their systems can handle complex tasks and process data efficiently, leading to improved productivity and satisfaction rates especially with customer facing tasks.
RAM is a Requirement for Multitasking and Concurrent Operations
People aren’t great task switchers, but computers with enough RAM are. Getting your gigabytes right enables your computers to handle multiple tasks simultaneously, commonly referred to as multitasking.
With ample RAM, computers can efficiently switch between various applications and processes without experiencing performance bottlenecks.
This capability is particularly important in business environments where employees need to work with several software applications concurrently, improving workflow efficiency.
The Right Amount of RAM Comes at a Cost
The cost of having sufficient RAM for onsite servers and desktop machines can vary depending on several factors. The price of RAM modules themselves fluctuates over time due to market conditions.
Additionally, consider the specific requirements of the business. RAM calculations should be based on factors such as the number of employees, fluctuation in workload demands, and the complexity of your applications. All these can significantly affect the amount of RAM needed.
Before making an expensive capital investment, carefully assess your business needs and consider the scalability of RAM so that the investment aligns with your organization’s budget and growth plans.
 Does Your IT Staff Have Bandwidth for Maintenance and Upkeep?
Does Your IT Staff Have Bandwidth for Maintenance and Upkeep?
Maintaining RAM involves ensuring its proper functioning and compatibility with the computer system.
While RAM itself doesn’t require extensive maintenance, occasional cleaning of the RAM slots to remove dust and debris can help prevent potential connectivity issues and prolong the life of your machines. Slowing machines can be dirty, not necessarily overwhelmed by memory hogging programs or too many open browser tabs.
No matter your current RAM situation, you or your IT professionals should periodically check for firmware updates and compatibility with the operating system to ensure optimal performance.
 Cloud Hosting Is a Cost Effective Solution for RAM Optimization
Cloud Hosting Is a Cost Effective Solution for RAM Optimization
Cloud hosting services are positioned to play a significant role in optimizing RAM usage for businesses.
By leveraging cloud hosting, your organization can offload the burden of managing onsite servers and desktop machines while gaining access to scalable and flexible computing resources.
Cloud hosting providers allocate and manage the required RAM resources on their own infrastructure, so your business has the necessary computing power and memory to meet steady or seasonal demands.
Cloud hosting allows for seamless scaling, reduced upfront costs, and enhanced performance, as cloud servers are equipped with ample RAM to handle varying workloads.
In Conclusion
RAM’s importance in business computing cannot be overstated.
It enhances performance, allows for efficient multitasking, and ensures smooth operation of your most resource-intensive applications.
While the cost of having sufficient RAM for onsite servers and desktop machines varies, every business must consider their specific requirements and future growth plans.
Although routine maintenance of RAM is generally straightforward, requiring only occasional physical cleaning and firmware updates, these tasks need to be completed by IT professionals to maintain the optimal performance of the system.
For many small to midsize businesses, cloud hosting offers an attractive solution by providing optimized RAM usage, scalability, and reduced IT management overhead.
By understanding the role of RAM and leveraging cloud hosting services, a smart business can unlock greater efficiency, productivity, and flexibility in their computing operations.
We Have Experts on Staff to Answer Your Questions About RAM
Interested in finding out how partnering with an award-winning cloud hosting provider can help you achieve your business goals while reducing your overall technology costs?
Our trained team of cloud computing experts can help by answering all your questions about how to align your technology with industry guidelines and while maintaining compliance standards.
We’ll show you how to use our efficient cloud based storage and processing solutions in your business to improve your security, productivity, and profitability.
Let us demonstrate exactly what CyberlinkASP can do for you – using your own data and workflows.
Service Management: The Key to a Successful Cloud ExperienceService management, particularly in the context of cloud hosting, is a concept that can initially seem complex, but it’s a vital part of the equation when it comes to confidently delivering a cloud experience that is seamless and efficient.
 What is Service Management?
What is Service Management?
In the simplest terms, service management is the practice of designing, delivering, managing, and improving the way information technology (IT) services are used within your organization.
Service management makes sure the right processes, people, and technology are in place so your organization can meet its business goals.
For a typical small-to-medium-sized business (SMB) – especially those without a dedicated IT department or large IT budget – the “right” processes and technology considerations might include:
- Incident Management: Implementing a process for dealing with IT incidents to minimize disruptions and loss of productivity or reputation.
- Regular Monitoring and Maintenance: Developing a schedule that works with your schedule to keep your systems running smoothly while preventing costly downtime.
- Reliable Access to Legacy Applications: Providing advanced cloud-based functionality without the need for significant or on-going capital technology investment.
How Does Service Management Work in Cloud Hosting?
In the context of cloud hosting, service management has a pivotal role. It ensures the resources you’re using – be it storage, applications, or security – are effectively managed, reliable, and delivering the value you’re expecting.
Whether it’s adjusting capacity, handling routine maintenance, or troubleshooting issues, service management keeps the various components of your cloud services performing optimally. This way, your cloud hosting environment remains robust and effective, giving your organization the technology capacity needed to thrive.
A robust service management strategy also involves continual service improvement. This means constantly evaluating the performance, finding gaps, and making necessary improvements to keep your business ahead in the game.
 Does Service Management Address Cybersecurity Concerns?
Does Service Management Address Cybersecurity Concerns?
With today’s cyber threat landscape every business, regardless of size, has valid cybersecurity concerns. Heading into 2021, malware attacks were reported to be up nearly 385% fueled largely by cybercriminals taking advantage of remote and hybrid work environments that aren’t using proper security measures.
With service management, security isn’t an afterthought. The most up-to-date threat management and intrusion detection is built into the very fabric of the service.
From data encryption to routine security audits, service management helps keep your mission critical and sensitive data safe in the cloud.
 Can Service Management Improve Organizational Productivity?
Can Service Management Improve Organizational Productivity?
Costly downtime and loss of productivity is a profit killer. The most recent estimate is that downtime can cost some businesses $10,000 an hour. Whatever your organization’s actual cost, it’s not something you want to pay if it can be avoided.
No company wants their network or services unavailable to employees or customers when they need them the most. This is where service management comes in.
Through monitoring and preventive maintenance, service management aims to keep downtime to a minimum, so your business stays up and running no matter your regular hours of operation.
 Can Service Management Reduce the Technical Burdens Facing Your Business?
Can Service Management Reduce the Technical Burdens Facing Your Business?
If you’ve been trying to juggle technology that seems to be getting more complicated – and vulnerable – by the day without the assistance of a strong IT department, this is where a strong vendor partnership comes into play.
Nearly 6 out of 10 businesses prefer to outsource aspects of their business that are outside their core competencies so they reserve more time on task for their core business activities.
A good cloud hosting provider will take on the heavy lifting of IT service management, leaving you free to focus on what matters most – your business.
You should expect to receive an easy-to-understand service level agreement. Monthly reports will be written in plain terms. Experts on hand will be there to resolve any technical questions or issues without the confusing jargon.
Plus, a good cloud partner will make migration a painless experience for your entire operation.
When you hire the right cloud-hosting company you’re not just buying a service; you’re gaining a partner committed to your success.
In Conclusion
Service management isn’t just another technology sector buzzword. It’s a powerful process used to enhance your cloud experience, while helping your organization to operate more efficiently and securely online.
Instead of adding complexity to your IT processes, it’s about giving you control, clarity, and peace of mind. If you’re ready to migrate business critical operations to the cloud, the service management team at your cloud-hosting partner will be there to maintain smooth and secure operations.
We Have Experts on Staff to Answer Your Questions About Service Management
Interested in finding out how partnering with an award-winning cloud hosting provider can help you achieve your business goals while reducing your overall technology costs?
Our trained team of cloud computing experts can help by answering all your questions about how to align your technology with industry guidelines and while maintaining compliance standards.
We’ll show you how to use our efficient cloud-based storage and processing solutions in your business to improve your security, productivity, and profitability.
Let us demonstrate exactly what CyberlinkASP can do for you – using your own data and workflows.
VPNs: What You Need to Know to Keep Your Business Safe OnlineMany industries consider VPNs to be vital for maintaining privacy and security online, especially when using public Wi-Fi or when there is a need to bypass geographical restrictions on internet access.
 Understanding the Role of VPNs
Understanding the Role of VPNs
A Virtual Private Network (VPN) is a mechanism to create a secure connection between an endpoint device and a network. People use VPNs where a secure connection is unlikely to exist.
This can safeguard your online activity from any possible tracking and exploitation. In a perfect world, this encryption makes your data unrecognizable to onlookers.
Regulated and innovative industries like:
- Healthcare
- Legal
- Finance
- Education
- Technology
have relied upon VPNs to protect sensitive information and intellectual property from unauthorized access.
Despite promises to the contrary from vendors, VPNs can fall far short of being a comprehensive security strategy. In fact, the false sense of security they convey to users can leave your data and network vulnerable to “human error” cyber-attacks.
Nearly 54% of VPN users report feeling secure while surfing the web. Nearly the same number have been the target of a cybercrime while online even when accessing the internet via a VPN.
 Why Would You Use a VPN in Your Business?
Why Would You Use a VPN in Your Business?
Many companies believe a VPN can be an asset when it comes to protecting business data. Vendors tout that their product can offer a significant boost to your privacy and security posture online.
VPN use makes it difficult for some hackers, internet service providers, or even governments to track your online activities. The trouble comes when VPN users often let their guard down and expose themselves to dangerous, but avoidable, links. Because a VPN is not an antivirus program, these user errors can expose your sensitive data and systems to malware.
Having users with a false sense of security is particularly relevant to businesses that have to deal with sensitive data or strict privacy regulations.
One use case that may make VPN relevant for your business is if you conduct business on a global scale. While traveling internationally, your employees can be subject to restricted internet access. Having a VPN can allow business travelers to circumvent government regulations and render your online activities undetectable when needed.
 Growing in Popularity: VPN Statistics, Trends, and Usage
Growing in Popularity: VPN Statistics, Trends, and Usage
Despite the potential risks, global VPN adoption continues to accelerate. Some 77% of internet users worldwide report they’ve used a VPN to shield their private data from prying eyes – especially when using public Wi-Fi.
VPNs are still predominantly used for personal reasons rather than business purposes. They are most likely to be used to boost personal security and access location-restricted content.
VPN use is most prevalent on desktops and laptops, although mobile usage is close behind. Perhaps surprisingly, about half of all users opt for free VPNs over paid alternatives, despite the increased risks associated with free versions.
When using a free VPN provider, your data isn’t just vulnerable to hackers. The reality is that one of the largest personal data breaches was the result of an attack on a free VPN provider, exposing nearly 360 million records to the dark web.
Data Centers and VPNs: Understanding Their Different Roles in Data Security
To understand how VPNs fit into the larger cybersecurity landscape, it’s important to distinguish them from other secure environments, like data centers.
An SSAE18 certified, compliant, and audited data center should be used by organizations to host their computer, server, and networking systems. Such a data center adheres to the strictest security standards and protocols mandated by certain government regulations, like HIPAA or GDPR. The data center operations undergo an annual audit to demonstrate its compliance.
The purpose of the data center is to store, process, and manage large amounts of data securely.
In contrast, a VPN primarily aids in secure and private browsing and communication.
The question isn’t about determining which option is better— a regulatory compliant data center or a VPN – but rather which tool fits the specific need.
You might need a data center for secure storage and processing of your organizational data and a VPN for ensuring secure internet access.
VPNs and Desktop Virtualization
In the realm of desktop virtualization or Desktop-as-a-Service (DaaS), VPNs can play a significant role. They offer secure access to cloud resources and protect sensitive data during transmission.
By integrating a VPN solution with cloud hosting, businesses can achieve secure, remote access to their data and applications stored in the cloud, adding an additional layer of protection.
With continued remote or offsite work, an ever expanding global workforce, and reliance on cloud services, the use of VPNs in virtual desktop infrastructure is likely to remain a point of interest for SMBs.
While VPNs are not a one stop security solution, with proper antivirus protection and staff training, they can fill a need in certain business environments to provide access and data protection.
In Conclusion
Selecting the right tools for your business’s digital and information security is no small decision. Depending on your specific needs and constraints, a VPN might be the perfect choice, or you might find a better fit.
 Staying secure in the digital world is an ongoing task, and understanding tools like VPNs and their alternatives is a step in the right direction toward keeping your sensitive data secure.
Staying secure in the digital world is an ongoing task, and understanding tools like VPNs and their alternatives is a step in the right direction toward keeping your sensitive data secure.
We Have Experts on Staff to Answer Your Questions About VPNs
As an award winning cloud hosting vendor, we are committed to empowering businesses with the knowledge and resources needed to navigate the digital landscape safely and effectively.
Our trained team of cloud computing experts can help by answering all your questions about how to align your technology with industry guidelines and while maintaining compliance standards – no matter where your business takes you.
Our secure and reliable hosting solutions are designed to give your business the privacy and performance it needs.
Let us show you exactly how CyberlinkASP can help – using your own data and workflows and our decades of experience.
Can Adopting Smart Cloud-based Storage Solutions Revolutionize Your Business?With every aspect of your business relying on technology, having the right amount of computer storage at the right time isn’t optional.
However, traditional storage solutions can often fall short, leading businesses into a storage crisis. This is where cloud hosting services emerge as a dynamic solution.
Not only can cloud services combat storage shortages, they can also help reduce the Total Cost of Ownership (TCO) and free up IT departments to focus on other critical technology initiatives.
If you constantly find yourself frustrated with the speed of your office computer or you’re tired of hearing staff apologizing to your best customers and clients about slow response times, you may need a storage solution to improve business operations.
 Understanding Computer Storage and its Limitations
Understanding Computer Storage and its Limitations
Computer storage is the digital depository for all your essential data and applications, so it plays a critical role in maintaining smooth business operations.
On the other hand, storage shortages can disrupt your key systems, cause operational inefficiencies, and even lead to data loss.
If you’re operating off traditional storage methods, such as onsite servers and hard drives, you already know they come with inherent limitations.
Plus, traditional storage options are often expensive, inflexible, and vulnerable to physical damage – from everything from a malfunctioning cooling system to a full-scale natural disaster.
The Cost Impact of Storage on IT and Total Cost of Ownership (TCO)
When analyzing the financial impact of IT operations, it’s imperative to understand the TCO, which refers to the complete cost of owning and operating a product or system over its lifecycle.
Both the storage acquisition and maintenance of your network resources significantly contribute to the TCO in your IT department.
These costs extend beyond just purchasing physical storage units or servers. Typically, it includes:
- energy costs for power and cooling
- expenses for space to act as your data center,
- ongoing system upgrades
- general maintenance costs
Even fewer tangible costs, like the time spent by your IT department managing and troubleshooting storage systems, can be contributing cost factors.
 Migrating to cloud hosting services can significantly reduce storage related TCO, making it a financially wise choice for businesses.
Migrating to cloud hosting services can significantly reduce storage related TCO, making it a financially wise choice for businesses.
Cloud Hosting Services as a Solution
Cloud hosting services offer an efficient, modern alternative to maintaining your own server room onsite.
Cloud services allow businesses to store all their business-critical data on remote servers, accessible via the internet. This arrangement frees up IT staff from routine storage management tasks and enables them to focus on primary technology initiatives.
This transition to the cloud not only solves storage issues but can also drive down the impact of large line items in your IT budget, allowing you to reallocate your dollars to other critical areas. By partnering with a reliable cloud vendor, you’re able to stabilize your business during uncertain economic times.
 Here are some of the key advantages of cloud-based storage for businesses of all sizes:
Here are some of the key advantages of cloud-based storage for businesses of all sizes:
Scalability: You can easily adjust your storage capacity based on evolving needs and goals. As Roy Stephan, Director IT Architecture & Engineering at Intelligent Decisions once said, “with the cloud…small businesses can snap their fingers and instantly set up enterprise-class services.”
Accessibility: Cloud-stored data is accessible anytime, anywhere, if you have an internet connection.
Cost-Efficiency: Most cloud services operate on a type of pay-as-you-go model, meaning you only pay for what they use based on assessment of needs
Security: Leveraging advanced encryption methods, cloud services offer robust protection for your data.
Redundancy: Cloud services back up data on multiple servers – often in multiple data centers – to safeguard against potential data loss.
Addressing Concerns and Objections to Cloud Hosting Services
Despite the clear benefits, some businesses do hesitate to adopt cloud storage.
Let’s address the most common concerns we hear:
Security: While it’s true that data is stored remotely – or “out of your hands” – cloud hosting providers prioritize data security, utilizing advanced encryption techniques and the most up to date layers of protection.
Cost: Although transitioning to cloud services may seem expensive upfront, it often leads to significant long-term cost savings by reducing TCO. If cost is an issue, make sure you talk about your concerns with sales and find out exactly what you’re getting by reviewing your service level agreement (SLA).
Data Accessibility: Reputable cloud providers guarantee high uptime – aim for 99.9% and consider partnering with a provider who has a money back guarantee. This will ensure your data is always accessible.
Transitioning to the Cloud: The move to the cloud can seem daunting. However, most providers offer comprehensive support, making the transition smoother.
In Conclusion
Overcoming productivity and reputation diminishing storage shortages while reducing TCO are key challenges for most businesses today.
 Cloud hosting services offer a practical, cost-effective, and secure solution.
Cloud hosting services offer a practical, cost-effective, and secure solution.
Cloud services not only combat storage issues but also allow IT departments to refocus on strategic technology initiatives. By dispelling misconceptions and addressing potential concerns, we aim to highlight the immense potential of cloud services.
If you’re struggling with storage issues, consider the benefits of switching to a cloud hosting service.
We Have Experts on Staff to Answer Your Questions About Storage
Interested in finding out how partnering with an award-winning cloud hosting provider can help you achieve your business goals while reducing your overall technology costs?
Our trained team of cloud computing experts can help by answering all your questions about industry guidelines and compliance standards starting with our clear, easy to understand Service Level Agreement.
We’ll show you how to use our efficient cloud-based storage and processing solutions in your business to improve your security, productivity, and profitability.
Let us demonstrate exactly what CyberlinkASP can do for you – using your own data and workflows.
Reducing the High Cost of Downtime with Cloud HostingIn regulated industries like healthcare or finance, or in data driven sectors like manufacturing or legal, your system availability and reliability aren’t just conveniences – they’re necessities.
The key to understanding what this means to your organization is defined by two critical metrics: uptime and downtime.
 Understanding Downtime
Understanding Downtime
In simplest terms, downtime is a period when your IT system, or part of it, is not functional.
Imagine you’re in the middle of accessing patient health records, legal documents, manufacturing control systems, or financial auditing tools, and suddenly, everything goes offline.
That’s network downtime, and it can have far-reaching effects on your ability to conduct business as usual.
 Downtime vs. Uptime
Downtime vs. Uptime
If downtime is the period when your systems and applications are inaccessible due to issues, maintenance, or updates, uptime refers to the period when your systems and applications are fully operational, accessible, and functional.
You may also see “uptime” referred to as “network availability”.
When it comes to cloud hosting services, the quality – and the cost — is often measured by its uptime percentage.
The most competitive services aim for “Five Nines” (99.999%) uptime, translating to only 5.26 minutes of downtime per year.
However, this level of service can be costly and often exceeds many businesses’ requirements.
A more common and affordable level of service is “Three Nines” (99.9%) uptime, equating to approximately 8.76 hours of downtime per year.
Planned vs. Unplanned Downtime
Downtime can be planned or unplanned. Planned downtime is scheduled and announced in advance for system updates, hardware upgrades, or maintenance.
Typically, these routine tasks are scheduled during off-peak hours to minimize potential disruption.
Unplanned downtime, on the other hand, occurs without warning due to unforeseen events like hardware failures, network outages, or cyberattacks.
According to a study by Gartner, the average cost of IT downtime is around $5,600 per minute. With that pricetag, the importance of minimizing unplanned downtime comes into sharp focus.
The True Cost of Downtime
The cost of downtime isn’t just about lost revenue. It also includes lost productivity, recovery costs, regulatory fines, especially for those operating in regulated industries where downtime can lead to compliance issues, and damage to your business reputation.
Having a strong Service Level Agreement (SLA) in place becomes essential for your business continuity.
Service Level Agreements (SLAs) and Cloud Hosting
An SLA is the contract between a service provider and the customer that defines the level of service to be expected. Think of the SLA as a form of insurance against potential downtime and its associated costs.
If you’ve ever reviewed an SLA, you probably know that they are often quite difficult to understand and rely heavily on confusing “tech speak”.
At CyberlinkASP, we pride ourselves on using a clear, jargon-free SLA.
We believe clear communication is the heart of every business relationship.
Our SLA clearly outlines our promise to our customers of 99.99% uptime – or your money back.
This guarantee offers assurance that your applications and services will be available when needed.
If we fail to meet this commitment, we’ve tied financial consequences to our performance to demonstrate our dedication to maintaining your systems and keeping them operational.
 The Role of Cloud Hosting in Downtime Reduction
The Role of Cloud Hosting in Downtime Reduction
With such high stakes, how can you minimize the risk and impact of downtime?
This is where cloud hosting services can become an integral part of your IT solution.
By entrusting your network to a cloud hosting partner, you’re effectively outsourcing the headache of maintaining system availability.
Your cloud provider handles the task of keeping your systems operational, which means you’re free to focus on your core business operations.
Moreover, Cybersecurity Ventures reports that the total cost of cybercrime in 2023 is predicted to hit $8 trillion. Small and midsized businesses are not immune from the threats posed by cybercriminals. Quite the contrary – SMBs are considered a target rich environment for malicious actors.
Given the substantial costs associated with data breaches and downtime, investing in reliable cloud hosting services can yield significant returns through business continuity, data security, and regulatory compliance.
In Conclusion
Choosing the right cloud hosting provider is not just about finding the provider with the best uptime – although that should be a primary KPI. Making the right choice for your organization is about finding a partner who understands your business or industry’s unique needs, communicates clearly about planned and unplanned downtime, and is transparent about their commitments in their SLA.
In regulated industries, downtime isn’t just an inconvenience – it’s a high-stakes risk. However, with the advanced technology and expertise offered by cloud hosting services, you can significantly mitigate this risk.
By trusting your systems to a proven cloud services vendor, you’re taking a significant step towards ensuring reliability, maintaining compliance, safeguarding your reputation, and bolstering your defenses against cyber threats.
We Have Experts on Staff to Answer Your Questions About Avoiding Downtime
Interested in finding out how partnering with an award-winning cloud hosting provider can help you achieve your business goals while reducing your overall technology costs?
Our trained team of cloud computing experts can help by answering all your questions about industry guidelines and compliance standards and it all starts with our clear, easy to understand Service Level Agreement.
We’ll show how using our efficient cloud based storage and processing solutions in your business can improve your security, productivity, and profitability.
Let us demonstrate exactly what CyberlinkASP can do for you – using your own data and workflows.
Why an Intrusion Detection System is a Must-Have for CybersecurityUnderstanding Intrusion Detection Systems (IDS) and their critical role in network security is important for every business. IDS solutions are reliable sentries in the fast-changing world of cybersecurity, defending sensitive data against malicious, and often costly cyberattacks.
This article will explain the basics of IDS and we’ll show why IDS is an important part of any proactive cybersecurity plan.
 Understanding Intrusion Detection System (IDS)
Understanding Intrusion Detection System (IDS)
An Intrusion Detection System (IDS) is fundamental to cybersecurity.
It’s a tool designed to safeguard digital networks and systems from harmful activities. An IDS operates by continuously monitoring and analyzing network traffic or activities on individual devices. IDS is a constant watcher, detecting any signs of malicious behavior that could potentially indicate a cyberattack is afoot.
The IDS employs sophisticated algorithms and pattern-matching techniques to identify suspicious activity that deviates from established “normal” network behavior. It could be anything from a surge in network traffic, repeated failed login attempts, or the detection of known harmful code.
When an anomaly or potential threat is detected, the IDS generates alerts, providing system administrators with vital, real-time information about the potential security incident.
Some IDS solutions are equipped with automated response capabilities. This allows them to respond to identified threats without human intervention. This automated response further enhances the security posture of the network or system.
According to a recent article in Forbes Magazine, cybersecurity damages are expected to reach $10.5 trillion annually by 2025, making investment in IDS increasingly important for businesses across all sectors.
 Types of IDS
Types of IDS
When it comes to IDS, understanding the two primary types – Network-based IDS (NIDS) and Host-based IDS (HIDS) – can help you better align your cybersecurity strategy with your specific needs.
NIDS monitors and analyzes network traffic for signs of intrusion. This type of IDS is often deployed at strategic points in the network to check various traffic levels.
NIDS are excellent for detecting network-level attacks, such as Distributed Denial of Service (DDoS) attacks, and can provide protection to all the devices connected to the network.
HIDS checks individual devices (hosts) for suspicious activity. It monitors system files, installed software, and other activity on endpoint devices to identify anomalies that may indicate an intrusion or breach of the larger IT perimeter.
HIDS can be especially effective at detecting insider threats and attacks that originate from a compromised device within the network and securing distributed IT systems.
For smaller businesses, making the choice between NIDS and HIDS can depend on your specific network architecture and security needs.
If you have a significant investment in network infrastructure you may find that NIDS offer a cost-effective way to provide wide-ranging protection. However, if you have a lot of sensitive data stored or accessed on individual devices you may prefer the more targeted protection that HIDS can provide.
Some businesses even take a hybrid approach to IDS to achieve more comprehensive protection.
 Integrating IDS into Cloud Hosting for Real-time Monitoring in Secure Data Centers
Integrating IDS into Cloud Hosting for Real-time Monitoring in Secure Data Centers
An Intrusion Detection System (IDS) can be integrated into your cloud hosting and provide for real-time monitoring of your network.
Secure data centers use a combination of physical security measures and cybersecurity tools to protect the servers and the data they handle. The IDS is constantly monitoring network traffic and system activities within the data center environment.
This real-time monitoring allows the IDS to detect potential security threats as they arise, providing instant alerts that can help system administrators respond quickly and mitigate any potential damage. Some advanced IDS even have automated response capabilities, allowing them to take immediate action against detected threats.
Gartner estimates that 80% of enterprises will adopt IDS into their cybersecurity protocols by 2024, up from just 60% in 2020. Integrating an IDS into your cloud hosting through a secure data center can significantly enhance your overall cloud security. This creates an additional layer of protection for your data, promotes continuous system availability, and can even help with regulatory compliance like HIPAA.
Because in cybersecurity risk is always evolving, it is important to remember that the effectiveness of an IDS is dependent on its proper configuration and maintenance. Any IDS should be regularly updated to recognize the latest threat patterns.
System administrators should be trained to respond effectively to any alerts the IDS generates. You, or your cloud provider, should regularly review and adjust the IDS configuration to minimize false positives and optimize it to effectively detect real threats.
In Conclusion
Deploying an Intrusion Detection System (IDS) is not just an option, but a necessity as part of your cloud hosting security strategy.
Cybersecurity threats will only continue to grow in number and sophistication. Investing in or implementing a robust IDS through a trusted cloud provider will be your first line of defense to safeguard your business from costly data breaches or unwanted downtime.
Selecting the right IDS can deliver significant benefits, including enhanced network visibility, improved regulatory compliance, and effective threat management. More importantly, it will provide peace of mind knowing that your valuable data and systems are well-protected.
The choice of IDS will depend on your company’s unique needs and resources. Your choice should align with your business’s growth strategies and the nature of your data. You should consider your available resources for effectively managing the IDS.
No matter how advanced, an IDS isn’t a wholesale replacement for a comprehensive cybersecurity strategy. It should be used in conjunction with other security measures, including firewalls, antivirus software, and even security awareness training programs.
Always take a holistic approach to your organization’s cybersecurity, so your business remains resilient in the face of new cyber threats.
We Have Experts on Staff to Answer Your Questions About IDS
Interested in finding out how partnering with an award-winning cloud hosting provider can help you achieve your business goals while reducing your overall technology costs?
Our trained team of cloud computing experts can help by answering all your questions about how to align your technology with industry guidelines and while maintaining compliance standards.
We’ll show you how to use our efficient cloud-based storage and processing solutions in your business to improve your security posture, productivity, and profitability.
Let us demonstrate exactly what CyberlinkASP can do for you – using your own data and workflows.
Managed Service Providers: Benefits, Drawbacks, and How to Choose the Right OneIn a tight IT labor market and with everything in general getting more expensive, it’s become increasingly common for small and medium-sized businesses (SMBs) to look for technology solutions that allow them to operate more efficiently while managing costs more effectively.
One solution that remains popular is adopting the Managed Service Provider (MSP) model.
In fact, nearly 88% of companies surveyed in advance of London Tech Week said they use or are currently assessing using MSPs to support their internal IT teams.
U.S. based companies tend to lead the supplemental use of MSPs. These partnerships help them stay up to date with the latest technology while improving overall network performance.
To help you decide if a MSP is right for your organization, we’ll look at the nuances of the MSP model. First by examining the pros and cons, then by discussing the best ways to evaluate if an MSP is the right choice for supporting your business or supplementing your IT department.
 What is a Managed Service Provider (MSP)?
What is a Managed Service Provider (MSP)?
A managed server provider is a company that remotely manages a client’s IT infrastructure. This can include monitoring of end-user systems. MSPs typically operate on a proactive basis and under a subscription model.
MSPs can cover a range of services such as network architecture, applications, infrastructure, and security protocols. This allows the MSP’s client to focus on their core business activities while the MSP handles their IT needs.
With a MSP handling day-to-day operations, internal IT departments can be deployed to handle larger, more complex issues.
 Pros of the MSP Model
Pros of the MSP Model
- You get the benefit of the MSPs expertise and experience.
MSPs can bring a wealth of knowledge and skill to the table. Their teams are experienced in a variety of IT environments and complex technologies. Closing this skill gap would be costly for the average SMB to accomplish in-house.
- The MSP shoulders most costs related to maintaining a modern, secure technology infrastructure.
Under the typical MSP model, you pay for what you need, when you need it. This allows for more predictable budgeting, lowered capital expenditures, and eliminates the expenses associated with hiring, onboarding, and maintaining full-time IT staff.
- Since MSPs have highly trained – and often round the clock staffing – they can provide proactive support.
Their technicians are constantly monitoring customer operations to identify and resolve issues before they cause downtime or loss of productivity. This can greatly enhance the reliability and efficiency of your IT systems.
- Working with an MSP allows you greater opportunity to scale operations without the direct overhead of expensive computing hardware purchases or need to hire highly skilled and in demand IT professionals.
As you reach business development benchmarks, an MSP can easily scale your IT services to meet your evolving needs. This flexibility combined with cost savings can prove invaluable in a rapidly changing business environment.
 Cons of the MSP Model
Cons of the MSP Model
- You may feel that working with an MSP represents a loss of control over your IT.
With an MSP handling your IT operations, some control over your infrastructure and systems is relinquished. This could potentially pose issues with specific operational procedures your business may need.
- Working with an MSP creates a certain level of dependence.
After integration of an MSP into your daily business operations, it can be difficult to transition away. Some complaints around MSPs suggest that users feel a certain degree of vendor lock-in.
- Working with the wrong MSP can delay communication and response time.
As with any service provider, not all MSPs are created equal. Some may not be equipped to provide the rapid response or clear communication your business requires. This can be particularly acute if they are in a different time zone from you or have a high client-to-technician ratio.
 Evaluating if an MSP is Right for Your Organization
Evaluating if an MSP is Right for Your Organization
Choosing to work with an MSP is a strategic decision and should be carefully considered.
Here are some factors to evaluate:
- Be clear and understand your current needs. Begin with an assessment of your organization’s IT needs:
- What IT tasks are you currently handling in-house?
- Could these be better managed by an MSP?Also consider your future needs so you select an MSP who has the agility to scale with you.You want to “start with the end in mind” by choosing an MSP that will be able to grow and adapt with your business.
- Always double check their expertise.
Research the MSP to confirm they have experience and expertise relevant to your industry. This not only pertains to their technical capabilities, but also their understanding of regulatory compliance – like HIPAA – and any specific security or privacy challenges your particular industry may face.
- Review and be sure you truly understand their Service Level Agreement (SLA).
The SLA should clearly define – in plain language — what services the MSP will provide. It should include their responsibilities, uptime, and expected response times. Make sure it aligns with your business needs and expectations.
- When hiring, look for a partner, not just a provider.
An MSP should be seen as a strategic partner that is invested in the success of your business. Look for an MSP that values relationship building and will work closely with you to help your business thrive.
In Conclusion
Incorporating an MSP into your business strategy can offer significant benefits, from cost savings to access to expert-level IT resources.
However, it’s important to weigh these benefits against the potential drawbacks and evaluate if the MSP model aligns with your business objectives.
By carefully considering your needs and thoroughly vetting potential providers, you can find an MSP that becomes an invaluable partner in your organization’s growth and success.
We Have Experts on Staff to Answer Your Questions About MSPs
Interested in finding out how partnering with an award-winning cloud hosting provider can help you achieve your business goals while reducing your overall technology costs?
Our trained team of cloud computing experts can help by answering all your questions about how to align your technology with industry guidelines and while maintaining compliance standards.
We’ll demonstrate how to use our efficient cloud-based storage and processing solutions in your business to improve your security, productivity, and profitability.
Let us demonstrate exactly what CyberlinkASP can do for you – using your own data and workflows.
Tethering: Network Access from AnywhereStaying connected to the internet is crucial, especially for organizations that rely on remote access to computing resources and data.
 What is Tethering?
What is Tethering?
Tethering is the practice of sharing the internet connectivity of one device, typically a smartphone or tablet, with another device, such as a laptop or another smartphone.
Tethering allows the device with internet access to act as a modem or router to provide internet access through various connection methods like USB, USB-C, Wi-Fi, or Bluetooth.
By tethering devices, users can utilize their mobile data plan or existing internet connection on one device to establish an internet connection on another device. This expands access to the internet in situations where traditional internet connectivity is unavailable or unreliable.
You may be wondering if tethering is necessary given the prevalence of public and private mobile hotspots.
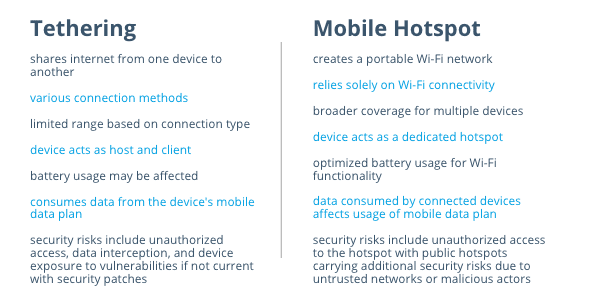 This chart breaks down the differences between the two:
This chart breaks down the differences between the two:
| Tethering | Mobile Hotspot |
| shares internet from one device to another | creates a portable Wi-Fi network |
| various connection methods | relies solely on Wi-Fi connectivity |
| limited range based on connection type | broader coverage for multiple devices |
| device acts as host and client | device acts as a dedicated hotspot |
| battery usage may be affected | optimized battery usage for Wi-Fi functionality |
| consumes data from the device’s mobile data plan | data consumed by connected devices affects usage of mobile data plan |
| security risks include unauthorized access, data interception, and device exposure to vulnerabilities if not current with security patches | security risks include unauthorized access to the hotspot with public hotspots carrying additional security risks due to untrusted networks or malicious actors |
As with any network connected endpoint, it is critical to implement appropriate security measures. Address employee use of tethering or mobile hotspots. Outline the steps to take when using these protocols to protect sensitive data as part of your organization’s BYOD policy.
 When is Tethering Useful in a Work Environment?
When is Tethering Useful in a Work Environment?
Employees may find themselves in areas with limited or no Wi-Fi coverage. Tethering allows them to utilize their mobile data connection and establish a reliable internet connection. This gives them access to company data, applications and computing resources or the ability to collaborate with colleagues or customers.
If your business often has people working in the field or where most of the work is performed off-site, traditional internet connectivity may not always be readily available. Having a tethering option provides your workforce with the means to establish a secure internet connection using their mobile device. This means they always have access to critical resources or real-time updates.
Tethering can play a role in other scenarios as well. Business travel, temporary offices, trade shows, conferences, or client visits are all legitimate uses for tethering to maintain uninterrupted network access to maintain productivity on the go.
In the event of a network outage or service disruption, tethering can serve as a backup internet connection. By using their personal devices and tethering capabilities, employees can maintain productivity and access essential applications while the primary network is being restored.
 Tethering, Security Risks, and Potential Cost Mitigation
Tethering, Security Risks, and Potential Cost Mitigation
Tethering is convenient, but it’s essential to address the network security risks the practice poses to your company’s sensitive data. Primary risks are unauthorized access, man-in-the-middle attacks, and data interception.
To mitigate risk, companies should establish clear guidelines to include requirements for establishing secure connections.
Policies should address:
- password protection on tethered connections
- using more robust encryption protocols such as WPA2 for Wi-Fi tethering
- restrict access to sensitive data while tethering
- requirements to keep devices updated with the latest security patches.
Since tethering consumes data from the employee’s mobile data plan, it can lead to exceeding plan limits and additional charges – a potential source of friction.
Be proactive. Consider developing guidelines on monitoring data usage to optimize consumption. If it is right for your organization, you might offer reasonable reimbursement for work-related data charges incurred from tethering in an approved use case.
In Conclusion
Embracing tethering gives you the flexibility to provide a productive work environment in and out of the office. By understanding the security risks, addressing compliance, and recognizing scenarios where tethering is needed, you can reap the benefits of tethering while safeguarding sensitive data and network security.
A tethering policy should outline acceptable use guidelines and emphasize the protection of sensitive company information. By addressing tethering in your BYOD policy, you can set clear expectations and maintain compliance standards.
When you have clear guidance in place, tethering can be a valuable tool to enhance productivity and maintain connectivity wherever work takes your employees.
 We Have Experts on Staff to Answer Your Cloud Computing Questions
We Have Experts on Staff to Answer Your Cloud Computing Questions
Interested in finding out how partnering with an award-winning cloud hosting provider can help you achieve your business goals while reducing your overall technology costs?
Our trained team of cloud computing experts can help by answering all your questions about developing internal compliance standards or developing a clear, easy to understand BYOD policy.
We’ll show you how using our efficient cloud-based storage and processing solutions in your business can improve your security, productivity, and profitability.
Let us demonstrate exactly what CyberlinkASP can do for you – using your own data, applications, and workflows.

 How Many Different Types of Reboots Are There?
How Many Different Types of Reboots Are There? Are There Risks Associated with Rebooting Your System?
Are There Risks Associated with Rebooting Your System? How Can Virtualized Desktops Reduce Reboot Related Data Risk?
How Can Virtualized Desktops Reduce Reboot Related Data Risk? What is an Operating System?
What is an Operating System? Identifying Your Computer’s Operating System
Identifying Your Computer’s Operating System What is the Benefit of Changing the OS of Business Computers?
What is the Benefit of Changing the OS of Business Computers? Tailored Cloud Hosting Services for Your Operating System
Tailored Cloud Hosting Services for Your Operating System What is a Mainframe Computer?
What is a Mainframe Computer? Is the Mainframe Computer Still Relevant Today?
Is the Mainframe Computer Still Relevant Today? The Mainframe’s Relevance in Modern Cloud Computing
The Mainframe’s Relevance in Modern Cloud Computing Need Help Making Your Network More Robust, Increasing Business Productivity, Or Capping Escalating Technology Costs?
Need Help Making Your Network More Robust, Increasing Business Productivity, Or Capping Escalating Technology Costs? What is Virtualization in Cloud Computing?
What is Virtualization in Cloud Computing? What is Server Virtualization?
What is Server Virtualization? Why Consider Desktop Virtualization?
Why Consider Desktop Virtualization? How Can Virtualization Enhance Security, Scalability, and Resource Efficiency?
How Can Virtualization Enhance Security, Scalability, and Resource Efficiency? How Much RAM Do We Need?
How Much RAM Do We Need? Cloud Hosting Is a Cost Effective Solution for RAM Optimization
Cloud Hosting Is a Cost Effective Solution for RAM Optimization What is Service Management?
What is Service Management? Does Service Management Address Cybersecurity Concerns?
Does Service Management Address Cybersecurity Concerns? Can Service Management Improve Organizational Productivity?
Can Service Management Improve Organizational Productivity? Can Service Management Reduce the Technical Burdens Facing Your Business?
Can Service Management Reduce the Technical Burdens Facing Your Business? Understanding the Role of VPNs
Understanding the Role of VPNs Why Would You Use a VPN in Your Business?
Why Would You Use a VPN in Your Business? Growing in Popularity: VPN Statistics, Trends, and Usage
Growing in Popularity: VPN Statistics, Trends, and Usage Understanding Computer Storage and its Limitations
Understanding Computer Storage and its Limitations Understanding Downtime
Understanding Downtime Downtime vs. Uptime
Downtime vs. Uptime The Role of Cloud Hosting in Downtime Reduction
The Role of Cloud Hosting in Downtime Reduction Understanding Intrusion Detection System (IDS)
Understanding Intrusion Detection System (IDS) Integrating IDS into Cloud Hosting for Real-time Monitoring in Secure Data Centers
Integrating IDS into Cloud Hosting for Real-time Monitoring in Secure Data Centers What is a Managed Service Provider (MSP)?
What is a Managed Service Provider (MSP)? Pros of the MSP Model
Pros of the MSP Model Cons of the MSP Model
Cons of the MSP Model Evaluating if an MSP is Right for Your Organization
Evaluating if an MSP is Right for Your Organization What is Tethering?
What is Tethering? When is Tethering Useful in a Work Environment?
When is Tethering Useful in a Work Environment? Tethering, Security Risks, and Potential Cost Mitigation
Tethering, Security Risks, and Potential Cost Mitigation We Have Experts on Staff to Answer Your Cloud Computing Questions
We Have Experts on Staff to Answer Your Cloud Computing Questions